Study Guide for Test #3 Chapters 4, 5, and 6 Return To Main Page
Completion
Complete
each sentence or statement.
1. A(n) ____________________ file is defined as
a named collection of data that exists on a storage medium.
2. A filename ____________________ is an
optional file identifier that is separated from the main filename by a period.
3. A file's ____________________ is the
arrangement of data in a file, and the coding scheme that is used to represent
the data.
4. Most software programs have what is called
a(n) ____________________ file format that is used to store files.
5. An operating system maintains a list of files
called a(n) ____________________ for each storage disk, tape, CD, or DVD.
6. A root directory can be subdivided into
smaller lists, called ____________________.
7. File ____________________ is usually measured
in bytes, kilobytes, or megabytes.
8. File ____________________ encompasses any
procedure that helps you organize your computer-based files so that you can
find and use them more efficiently
9. Most operating systems provide file
____________________ utilities that give you the big picture of the files you
have stored on your disks and help you work with them.
10. A file management utility should make it easy
to find what you are looking for by drilling down through your computer's
____________________ of folders and files.
11. The ____________________ process creates the
equivalent of electronic storage bins by dividing a disk into tracks, and then
further dividing each track into sectors.
12. Computer operating systems provide formatting
____________________ that you can use to reformat some storage
devices—typically floppy and hard disks.
13. A computer ____________________ is a set of
program instructions that attaches itself to a file, reproduces itself, and
spreads to other files.
14. A(n) ____________________ is essentially a
miniature program that usually contains legitimate instructions to automate
document and worksheet production.
15. ____________________ software is a set of
utility programs that looks for and eradicates a wide spectrum of problems,
such as viruses, Trojan horses, and worms.
16. A virus ____________________ usually arrives
as an e-mail message containing dire warnings about a supposedly new virus that
is on the loose.
17. A(n) ____________________ is a copy of one or
more files that has been made in case the original files become damaged.
18. You ____________________ data from a backup to
the original storage medium or its replacement.
19. A(n) ____________________ disk is a floppy
disk or CD that contains the operating system files needed to boot your
computer without accessing the hard disk.
20. A(n) ____________________ CD contains the
operating system files needed to boot the computer, plus all of the Windows and
application software needed to restore your computer to the state it was in
when you bought it.
21. ____________________ is the distance between
wave peaks.
22. A communications ____________________, or
link, is a physical path or a frequency for a signal transmission.
23. RF signals are sent and received by a(n)
____________________ (a combination of a transmitter and a receiver) that is
equipped with an antenna.
24. Radio and microwave transmissions cannot bend
around the surface of the earth to reach far-flung towers, so earth-orbiting
communications ____________________ play an important role in long-distance
communications.
25. Each device that is connected to a network is
referred to as a(n) ____________________.
26. A(n) ____________________ is a device that
converts the signals from a computer into signals that can travel over a wide
area network, such as the telephone system or the Internet.
27. A(n) ____________________ is a device—found on
LANs and on the Internet—that amplifies and regenerates signals so that they
can retain the necessary strength to reach their destinations.
28. A(n) ____________________ is a parcel of data
that is sent across a computer network.
29. ____________________ switching essentially
establishes a private link between one telephone and another for the duration
of a call.
30. In a technology called ____________________
switching, a message is divided into several packets that can be routed
independently to their destination to avoid out-of-service or congested links.
31. In the context of networks, the term
"protocol," or ____________________ protocol, refers to the set of
rules for efficiently transmitting data from one network node to another.
32. Protocols help two network devices negotiate
and establish communications through a process called ____________________.
33. A(n) ____________________, or
"internet" (with a lowercase "i"), is a network that is
composed of many smaller networks.
34. A(n) ____________________ is a network that
uses TCP/IP protocols and provides many of the same services as the Internet,
but is typically owned by a private business and its use is limited to the
employees of that business.
35. A(n) ____________________ is similar to a
private intranet, except that it allows password-protected access by authorized
outside users.
36. A(n) ____________________ network uses radio
frequencies instead of cables to send data from one network node to another.
37. A(n) ____________________ network treats every
computer as an "equal" so that workstations can run local
applications and also provide network resources, such as file access.
38. A(n) ____________________ address is a series
of numbers, such as 204.127.55.001.
39. A domain name request is routed through your
ISP to your designated domain name ____________________, which then searches
through its database to find a corresponding IP address.
40. Personal ____________________ software is
designed to analyze and control incoming and outgoing packets.
41. You can click an underlined word or phrase
called a(n) ____________________ link in a Web page to access related
documents.
42. HTML is an example of a(n)
____________________ language in which authors mark up their documents by
inserting tags that specify how the document should appear when displayed on a
computer screen or printed.
43. The original HTML specifications were revised
several times by the ____________________.
44. ____________________ tags change the
appearance of text and work much like the formatting options in a word
processor that create bold and italic text, adjust the size of text, change the
color of text and backgrounds, and so on.
45. ____________________ tags specify how to
display graphics, sound clips, or videos.
46. The <HTML> </HTML> tag is in the
category of ____________________ tags.
47. ____________________, published in November
1993, was one of the earliest graphical browsers.
48. A(n) ____________________ is an abstract
concept that represents one end of a connection.
49. A(n) ____________________ protocol generally
allows one request and response per session.
50. Web ____________________ software provides
tools specifically designed to enter and format Web page text, graphics, and
links.
51. CSS stands for
________________________________________.
52. A(n) ____________________ GIF is a graphic
file that consists of a sequence of frames or related images.
53. A(n) ____________________ link automatically
opens a pre-addressed e-mail form that can be filled in and sent.
54. Each of the links within an image map is
sometimes referred to as a(n) ____________________.
55. ____________________ is the follow-up version
to HTML 4.
56. A series of scripting statements (e.g.,
written in JavaScript or VBScript) is called a(n) ____________________.
57. A(n) ____________________ error occurs when a
browser or server cannot execute one or more statements in a script.
58. ____________________ is typically used to
describe financial transactions that are conducted over a computer network.
59. ____________________ is an extension of HTTP
that simply encrypts the text of an HTTP message before it is sent.
60. An electronic ____________________ is software
that stores and handles the information that a customer typically submits when
finalizing an e-commerce purchase.
Matching
Identify the letter of the choice that
best matches the phrase or definition.
|
a. |
extension |
e. |
physical storage model |
|
b. |
root |
f. |
cluster |
|
c. |
path |
g. |
file system |
|
d. |
logical storage model |
h. |
defragmentation |
____ 61. Main directory of a disk
____ 62. Describes what happens on disks
____ 63. Helps you form a mental picture of the way in
which your files are stored
____ 64. Keeps track of the names and locations of
files that reside on a storage medium
____ 65. A group of sectors on a disk
____ 66. Utility you use to rearrange files on a disk
so they are stored in contiguous clusters
____ 67. File identifier separated from the filename by
a period
____ 68. File specification
Identify the letter of the choice that
best matches the phrase or definition.
|
a. |
twisted-pair cable |
e. |
microwaves |
|
b. |
coaxial cable |
f. |
infrared light |
|
c. |
fiber-optic cable |
g. |
transponder |
|
d. |
RF signals |
h. |
bandwidth |
____ 69. A bundle of extremely thin tubes of glass
____ 70. Consists of a copper wire encased in a
non-conducting insulator, a foil shield, a woven metal outer shield, and a
plastic outer coating
____ 71. Provide data transport for large corporate
networks and as part of the Internet backbone
____ 72. Receives a signal, amplifies it, and then
transmits the signal from a satellite to a ground station
____ 73. Also called radio waves
____ 74. The transmission capacity of a communications
channel
____ 75. Contains four pairs of copper wires
independently insulated and then wound around each other
____ 76. Carries data signals only for short distances
and with a clear line of sight
Identify the letter of the choice that
best matches the phrase or definition.
|
a. |
operational |
e. |
P3P |
|
b. |
formatting |
f. |
CSS |
|
c. |
HTTP |
g. |
GIF |
|
d. |
cookie |
h. |
JPEG |
____ 77. Use this type of tag to specify the basic
setup for a Web page
____ 78. Small chunk of data generated by a Web server
____ 79. Acts as a template to control the layout and
design of Web pages
____ 80. The best image format for logos and banners
____ 81. Use this type of tag to adjust text size, for
example
____ 82. A sophisticated approach to cookie security
____ 83. The best image format for scanned images
____ 84. Protocol used to get Web resources to your
desktop
Short
Answer
85. What is the Windows Startup Disk?
86. When using a software application to open a
file, what kinds of files does the program display?
87. Give two uses for the file date.
88. What is the difference between the Save and
Save As options?
89. What does the physical storage model describe?
90. What is the File Allocation Table?
91. What is file shredder software?
92. What are Denial of Service attacks?
93. What is a boot disk?
94. What is a recovery CD?
95. List six of the most common links that
computer networks use for carrying data.
96. What is the most practical use of infrared
light with respect to personal computers?
97. What happens if a device's physical address is
not in a format that can be used by a particular network?
98. The terms "host" and
"server" are often used interchangeably, but what is the distinction
between them?
99. Provide three examples of the most common
servers on today's networks.
100. Briefly explain how the asynchronous
protocol works.
101. Define HomePLC network.
102. Define 10BaseT network.
103. Define client/server network.
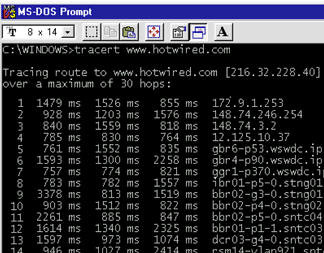
Figure 5-16
104. What does the utility in Figure 5-16
do?
105. Upon what does the number of socket
connections that a port can handle depend?
106. What is a server farm?
107. What is a cookie?
108. What is a Web page header?
109. When XML is described as being
"extensible," what does this mean?
110. What are the most popular scripting
languages? Name two other alternative scripting languages as well.
111. Define client-side script.
112. Name a way in which Java applets
differ from ActiveX controls.
113. What is B2G e-commerce?
114. What is an online shopping cart?
Study Guide
for Test #3 Chapters 4, 5, and 6
Answer
Section
COMPLETION
1. computer
2. extension
3. format
4. native
5. directory
6. subdirectories
7. size
8. management
9. management
10. hierarchy
11. formatting
12. utilities
13. virus
14. macro
15. Antivirus
16. hoax
17. backup
18. restore
19. emergency boot
boot
20. recovery
21. Wavelength
22. channel
23. transceiver
24. satellites
25. node
26. modem
27. repeater
28. packet
29. Circuit
30. packet
31. communications
32. handshaking
33. internetwork
34. intranet
35. extranet
36. wireless
37. P2P
peer-to-peer
38. IP
TCP/IP
39. server
40. firewall
41. hypertext
42. markup
43. W3C
World Wide Web Consortium
44. Formatting
45. Media
46. operational
47. Mosaic
48. socket
49. stateless
50. authoring
51. cascading style sheet
52. animated
53. mailto
54. hot spot
55. XHTML
56. script
57. scripting
58. E-commerce
59. S-HTTP
Secure HTTP
60. wallet
MATCHING
61. B
62. E
63. D
64. G
65. F
66. H
67. A
68. C
69. C
70. B
71. E
72. G
73. D
74. H
75. A
76. F
77. A
78. D
79. F
80. G
81. B
82. E
83. H
84. C
SHORT
ANSWER
85. The Windows Startup Disk is a type of boot
disk that loads not only the operating system but also the CD-ROM drivers
necessary for your computer to access files on the CD-ROM.
86. When using a software application to open a
file, the program displays any files that have the filename extension for its
native file format.
87. The file date is useful if you have created
several versions of a file and want to make sure that you know which version is
the most recent. It can also come in handy if you download several updates of
player software, and you want to make sure that you install the latest version.
88. The Save As option allows you to select a name
and storage device for a file, whereas the Save option simply displays the
latest version of a file under its current name and at its current location.
89. The physical storage model describes what
actually happens on the disks and in the circuits.
90. If your computer uses the FAT32 file system,
then the special file that maintains a list of clusters and keeps track of
which ones are empty and which ones hold data is known as the File Allocation
Table.
91. File shredder software overwrites empty
sectors with random 1s and 0s to delete data from a disk in such a way that no
one can ever read it.
92. Denial of Service attacks happen when worms
generate a lot of activity on a network by flooding it with useless
traffic—enough traffic to overwhelm the network's processing capability and
essentially bring all communications to a halt.
93. A boot disk is a floppy disk or CD that
contains the operating system files needed to boot your computer without
accessing the hard disk.
94. A recovery CD contains the operating system
files needed to boot the computer, plus all of the Windows and application
software needed to restore the computer to the state it was in when you bought
it.
95. The most common include twisted-pair cable,
coaxial cable, fiber-optic cable, radio waves, microwaves, satellites, infrared
light, and laser beams.
96. Its most practical use seems to be for
transmitting data between a notebook computer and a printer, or between a PDA
and a desktop computer.
97. The device will be assigned a logical address.
98. "Host" is more commonly used in the
context of the Internet; "server" is used both in the context of the
Internet and LANs.
99. E-mail servers, communications servers, file
servers, and Web servers are some of the most common servers on today's
networks.
100. The rules for asynchronous protocol
require the transmitting computer to send a start bit that indicates the
beginning of a packet. Data is then transmitted as a series of bytes—the number
of bytes is specified by the protocol. A stop bit marks the end of the data.
101. A HomePLC network uses a building's
existing power line cables (PLCs) to connect network nodes.
102. A 10BaseT network is techie jargon
for an Ethernet network that uses a type of twisted-pair cable called
"10BaseT" and transmits data at 10 Mbps.
103. A client/server network contains one
or more computers configured with server software, and other computers,
configured with client software, which access the servers.
104. The utility, Traceroute, records a
packet's path—including intermediate routers—from your computer to its
destination.
105. The number of socket connections
that a port can handle depends on the server's memory and operating system, but
at a minimum, hundreds of requests can be handled at the same time.
106. A server farm is a group of multiple
servers used to handle the thousands of requests that come in each second to a
large volume site.
107. A cookie is a small chunk of data
generated by a Web server and stored in a text file on your computer.
108. A Web page header is simply a
subtitle that appears in a font that is a different size or color than the
normal text in the paragraphs that appear on the page.
109. This means that individual users and
groups of users can create their own tags.
110. JavaScript and VBScript are the most
popular scripting languages, but alternatives do exist, including PerlScript,
Python, REXX, and Awk.
111. A client-side script consists of
scripting statements embedded in an HTML document that are executed by the
browser, which must have the capability to deal with that scripting language.
112. ActiveX controls are installed on
your computer's hard disk, whereas Java applets are simply downloaded into
memory and run. Also, Java applets work on many computer platforms, but ActiveX
controls only work on Windows PCs using the Internet Explorer browser.
113. B2G e-commerce aims to help
businesses sell to governments.
114. An online shopping cart is a
cyberspace version of the good old metal cart that you wheel around a store and
fill up with merchandise.